Replying to emails on-the-go, BYOD strategies and remote working can make it harder than ever for organisations to keep tabs on their employee’s network activity. Cybercriminals are becoming smarter and more manipulative, they aim to by-pass your IT team and deliberately target those ‘unaware’ employees who are the ‘weak link’ in your security strategy. While your business may have the best technology defences, cybercriminals know that your people may be less well defended.
The importance of people
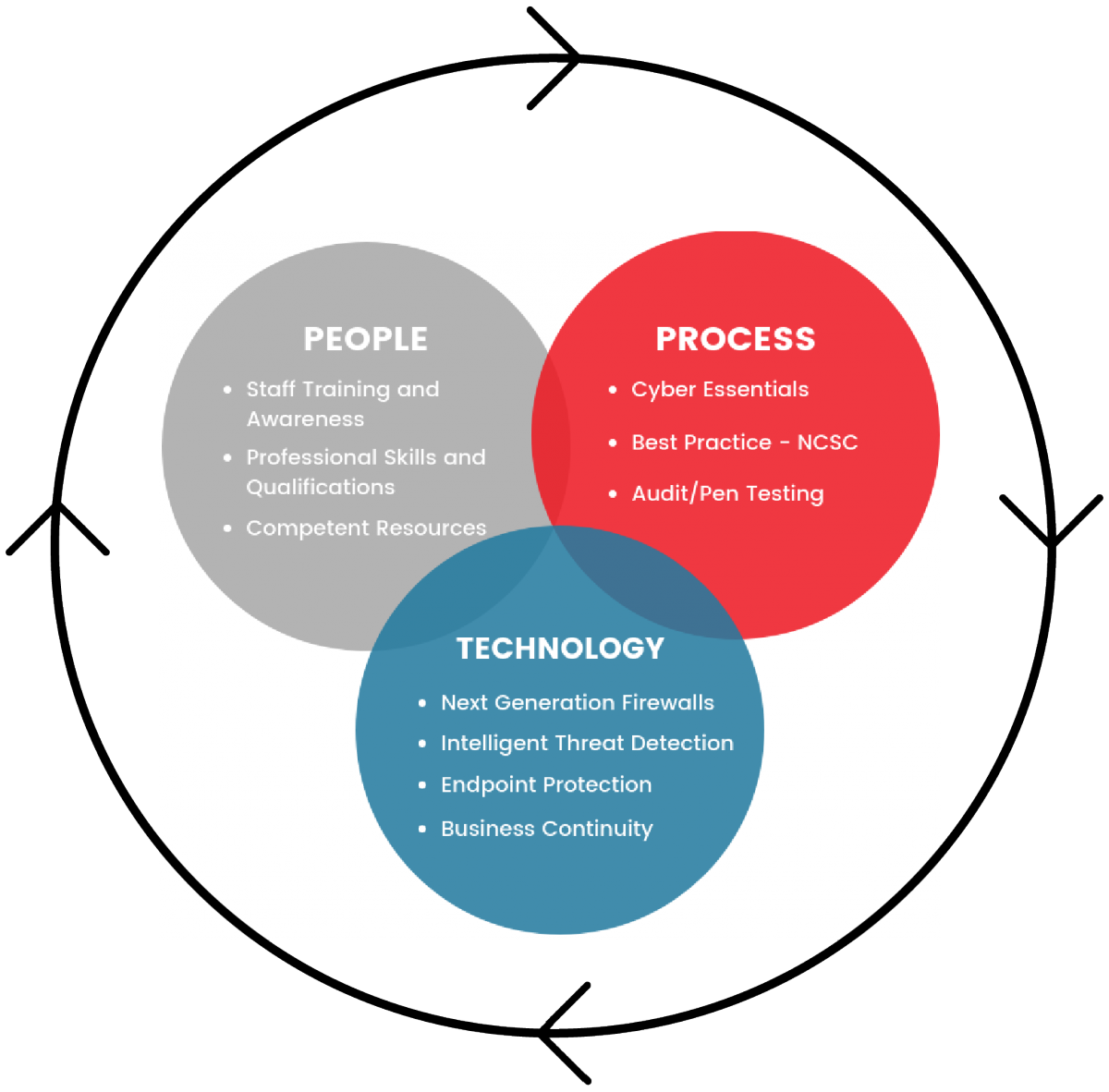
The cyber resilience framework (below) has three important components: People, Process and Technology, which combine to keep your business safe from cyber threats.
In this matrix ‘people’ form a key part of your defence strategy, your ‘human firewall’. Everyone in the business needs to be aware of their role in preventing and reducing cyber threats, whether it’s handling sensitive data, understanding how to spot phishing emails or the use of the BYOD. Industry reports show that 30% of phishing messages get opened by targeted users and human error accounts for 52% of security breaches. With the average breach costing UK SMBs £8k, not training your staff could harm your business.
The Cyber Security framework
What can businesses do?
Lead from the front
The responsibility of cyber-security should not be left solely to the IT department, you need to create a cybersecurity culture throughout the organisation. It’s common that the higher the position in the organisation, the higher the risk of a well-targeted and executed phishing attack. Everyone from senior management down needs to be on board with business owners and senior management leading by example.
Implement a cybersecurity policy
Your cybersecurity policy will provide staff with the guidelines they need to put their best foot forward when it comes to online activity. It also provides reassurance that the organisation is doing all they can to protect their people, data and assets.
Cyber education
Deliver cyber training and testing for your employees to give them the knowledge and skills to repel cyber-attacks. The most common method is to invest in an external training program. When choosing your training platform, it’s important to consider the following factors:
- Will it engage staff? Cybersecurity is a broad topic that needs continual training to ensure you’re putting your best foot forward, training should aim to increase staff engagement with interactive tasks and assessments.
- Can you check that staff have absorbed the information? Can staff demonstrate their knowledge through simple tests and reporting functions? This provides evidence to shareholders that staff are receiving effective, up-to-date training and can provide an insight into what staff understand.
- Does the training keep up with evolving technology? With technology advancing more rapidly, training platforms must be dynamic to provide information and guidance on the latest threats.
- Can you create training sessions specific to your staff? Not all companies are the same and neither is their cybersecurity. A good training platform should offer you the ability to create custom courses for your specific business needs.
To combat the rising threat of cyber-attacks, NTE has launched a suite of simple monthly services to address cybersecurity concerns across people, process and technology. You can be confident that you’re secure, giving you the time to focus on your day-to-day business.
The Business Transformation Network have shared this article in partnership with NTE.

