Written by Marten Cureton and Tom Sadler
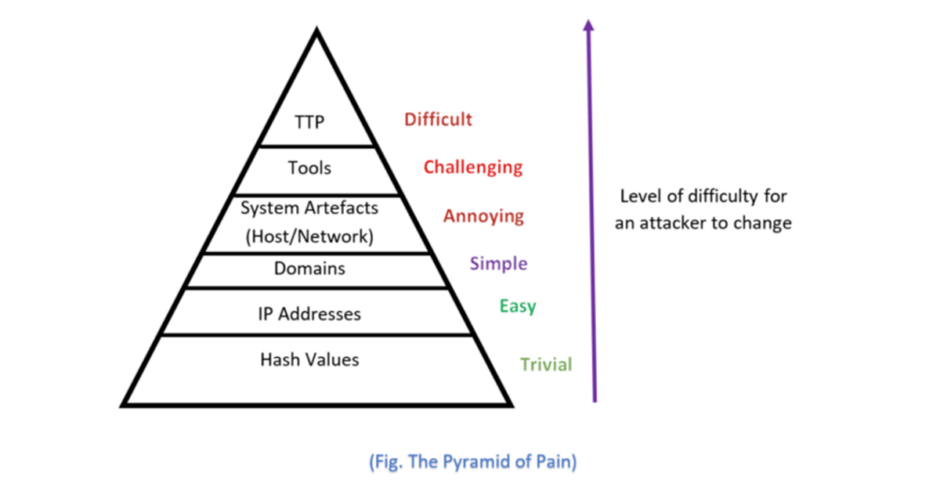
The Pyramid of Pain was created by security professional, David J Bianco, in 2013, while he was threat hunting and working on incident response. The Pyramid ranks, in ascending order, the list of indicators used to detect an attacker’s activities and how much “pain” it will cause the attacker by denying these different indicators, as well as the effort and difficulty to find each indicator for the security analyst.
Using our Managed Detection and Response (MDR) services, as well as our Security Essentials, we can easily analyse good data from the logs created and find hash values, IP addresses and domain names quickly and efficiently.
Our MDR service also distinguishes malicious activities from legitimate ones by analysing the processes and referencing the MITRE ATT&CK framework, which allows us to better identify the tools, Tactics, Techniques and Procedures used by attackers. This helps to mitigate these risks from your networks and systems.
As the Pyramid of Pain suggests – the closer we get to the top, the harder it is to detect and convert that information into something actionable. Similarly, the closer we get to identifying the upper layers of the pyramid of pain, the more challenging it is for the attacker to modify that behaviour.
Within our Security Essentials and Managed Detection and Response (MDR) services we are equipped to recognise every layer of the pyramid of pain and utilise this intelligence to not only protect your organisation but make it increasingly more difficult for threat actors to compromise your network.
Our solutions operate across the networking and endpoint space, offering full estate visibility. In a case example where a threat actor may have compromised a device within your organisation, our service can quickly identify all layers of the pyramid.
While not all indicators are created equally, meaning that some are easier to identify and modify, other indicators are more challenging to change especially where an attacker may be solely relying on a particular tool or framework. The granular view of each event and the links to the MITRE ATT&CK framework that our services provide, make it easier for our analysts to spot these indicators and turn this information into actionable intelligence.
Once identified, we are then able to feed that intelligence back into your organisation and help you to understand how to mitigate further attacks and identify any risks that may have exposed you to the threat in the first place.
We are further able to utilise this intelligence to update our own services by creating new detection rules based on any layer of the Pyramid of Pain, making it increasingly difficult for an attacker to reuse the same methods in the future and reducing the probability of the same style of attacks being successful.
Would you like to find out more about Security Essentials and Managed Detection and Response? If you have any questions, contact us here.